Table of Contents
Armitage – A Step by Step guide on How to Use to Hack Windows with Backtrack 5 R2/3:
General description: MITM
MITM [Man in the middle] attacks from wikipedia:
The man-in-the-middle attack (often abbreviated MITM, MitM, MIM, MiM, MITMA) in cryptography and computer security is a form of active eavesdropping in which the attacker makes independent connections with the victims and relays messages between them, making them believe that they are talking directly to each other over a private connection, when in fact the entire conversation is controlled by the attacker. The attacker must be able to intercept all messages going between the two victims and inject new ones, which is straightforward in many circumstances (for example, an attacker within reception range of an unencrypted Wi-Fi wireless access point, can insert himself as a man-in-the-middle).
A man-in-the-middle attack can succeed only when the attacker can impersonate each endpoint to the satisfaction of the other — it is an attack on mutual authentication (or lack thereof). Most cryptographic protocols include some form of endpointauthentication specifically to prevent MITM attacks. For example, SSL can authenticate one or both parties using a mutually trusted certification authority.
In this tutorial I will:
- Scan my whole lab network
- map it using Armitage
- set up a VNC viewer as my payload to view a target computer’s screen.
Note that this may not work if you have some antivirus software in your victim’s PC.
for those of you who are more of the optimistic – here is how to perform the attack by using Armitage automatic exploitation tools.
[mc4wp_form]
Armitage Requirements :
A Linux machine installed with MetaSploit Framework and Armitage
The versions used in this post:
- Armitage ver. 1.47
- Ubuntu 13.10
Although Armitage is one of the many tools included in Backtrack 5 rc2/3
If you haven’t installed Armitage yet, please check out my Tutorial on How to install Metasploit framework and Armitage.
The steps are as follows:
Step 1: Start scanning the desired network
Step 2: Set the scan range address
Step 3: Lunch Attacks
Step 4: Targeting a victim machine
Step 5: Choosing the desired Payload
Step 6: Connect to the victim’s machine
Let’s Begin:
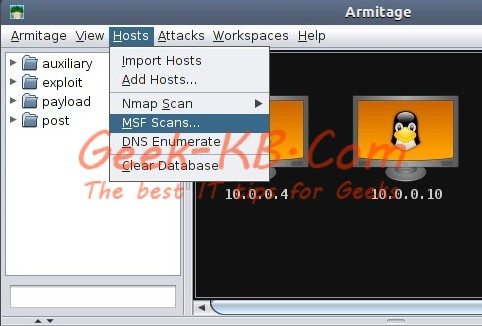
Armitage guide Step 1 – Start scanning the desired network
Choose Hosts → MSF Scans… (You can also use Nmap scans)
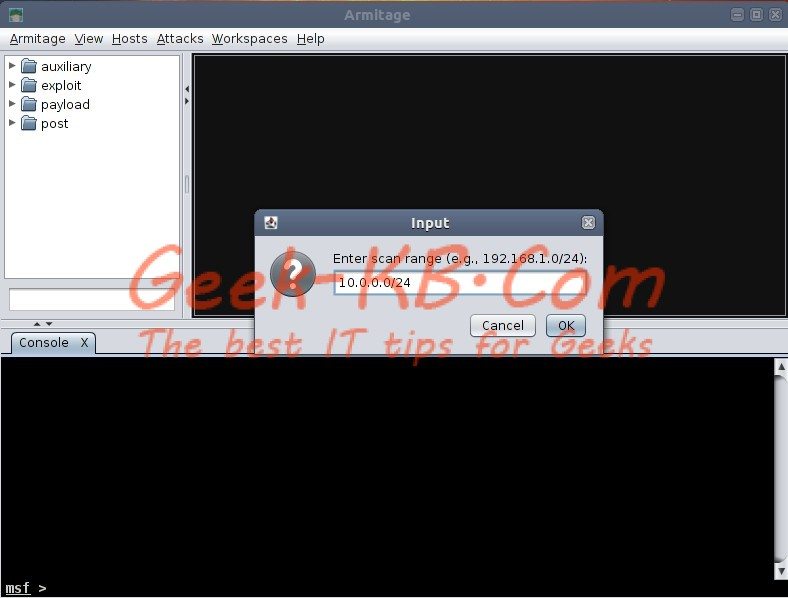
Armitage guide Step 2 – Set the scan range address
You can use a single IP address, CIDR notation or IP address range (e.g 192.168.0.10-192.168.0.20)
When the scan process finishes, all your network computers will be displayed with a background which matches each operating system.
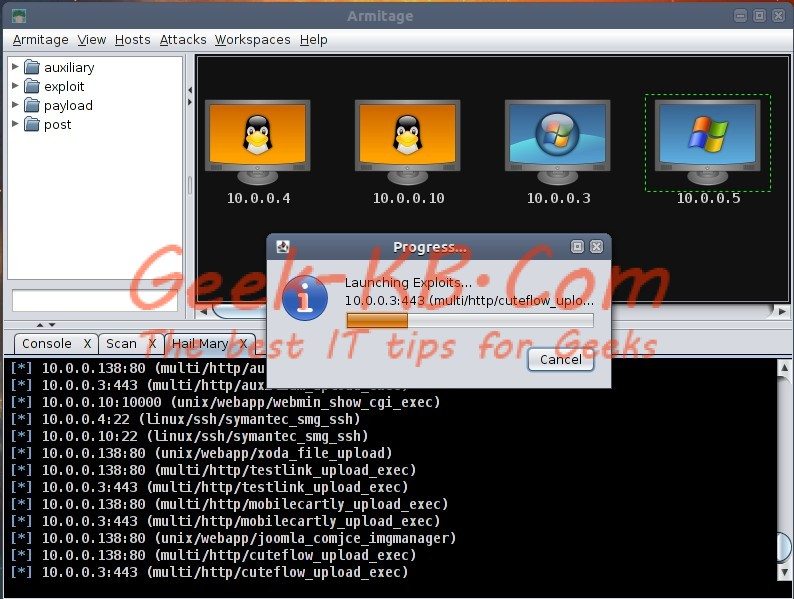
Armitage guide Step 3 – Lunch Attacks
Armitage has automatic exploitation feature called Hail Mary. According to Armitage website :
If manual exploitation fails, you have the hail mary option. Attacks -> Hail Mary launches this feature.
Armitage’s Hail Mary feature is a smart db_autopwn. It:
- finds exploits relevant to your targets
- filters the exploits using known information and then sorts them into an optimal order.
In this case we will use the Attacks –> Hail Mary feature:
even though you can also use manual exploitation for more specific targets:
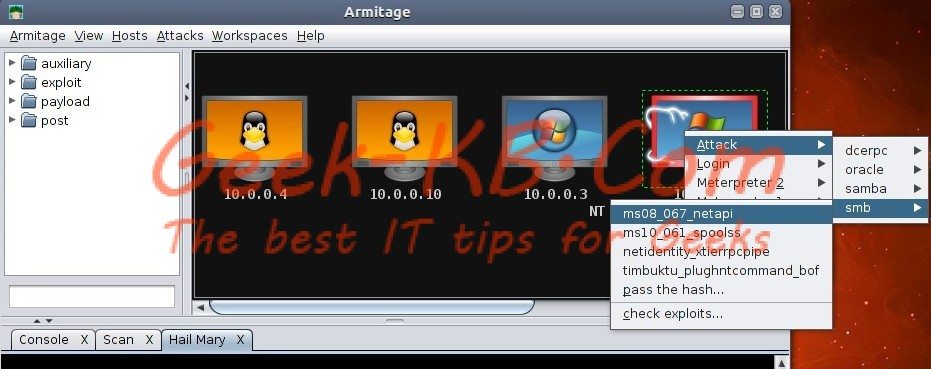
Armitage guide Step 4 – Targeting a victim machine
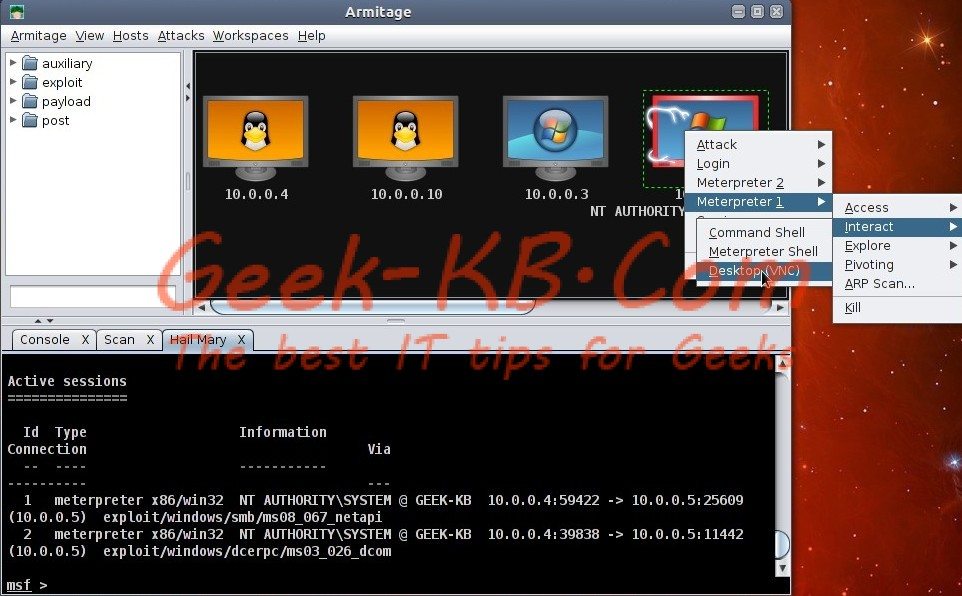
After Hail Mary finishes scanning the hosts and finds a vulnerable host on your network it will show a red color frame with lightnings on the vulnerable machine in the Armitage console.
if you found no vulnerable machine, then maybe you can try using a manual exploitation to exploit the target (like shown in the above image).
[mc4wp_form]
Armitage guide Step 5 – Choosing the desired Payload
Choose Meterpreter Payload
(Meterpreter enables users to control the screen of a device using VNC and to browse, upload and download files.)
Because the program already does most of the work for us (for major vulnerability and known vulnerability) we just need to connect to meterpreter which is ready to interact!
you can choose between Command Shell, Meterpreter Shell, or VNC. In this case, we will use VNC.
Armitage guide Step 6 – Connect to target machine
After choosing VNC desktop as a payload, there’s a pop up window which tells us to run VNC viewer to connect to our local address with a specific port(written there).
Now open up a new terminal and type vncviewer:port command to open a VNC session to the victim machine, like so:
There’s your VNC window for target machine remote desktop
I hope you liked this article, please feel free to leave comments, ask questions or sharing this article.
[mc4wp_form]
1. Geek-KB.com does not encourage, condone, or orchestrate attempts to hack into other servers or any other illegal activities. The articles contained inside this website are for entertainment / educational purposes only, and what actions people decide to take outside of this website are strictly independent of Geek-KB.com. We are not responsible if you break the law using techniques listed on this website.
2. Geek-KB.com has the sole discretion to remove/edit users, articles, external resources, or any other user-submitted content to protect itself from legal harm. This legal disclaimer may be modified at any time without notice.
3. Any damage caused by using any of the techniques taken from https://www.geek-kb.com is on your own responsibility, Use it at your own risk!





No Comments Yet