Table of Contents
OpenVPN How To: Install and configure on CentOS 6.4
In this page I write a step-by-step tutorial which will guide you through installing OpenVPN on CentOS 6.x server. I will demonstrate all the steps in order to be as clear as possible. Do not hesitate to ask if you have any question.
What do I need OpenVPN for?
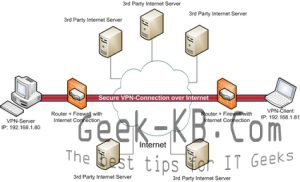
If you need to access your office network from a different location, the office located abroad or just far your 3G phone availability, than a virtual private network might be the solution you are looking for. In todays world many organizations still pay fees for VPN services, rather than use a server or system to fucntions as a VPN end-point. Setting up and configuring OpenVPN was never as easy with the RPMForge repository for CentOS 6.
Wikipedia short description:
OpenVPN is an open source software application that implements virtual private network (VPN) techniques for creating secure point-to-point or site-to-site connections in routed or bridged configurations and remote access facilities. It uses a custom security protocol[2] that utilizes SSL/TLS for key exchange. It is capable of traversing network address translators (NATs) and firewalls. It was written by James Yonan and is published under the GNU General Public License (GPL).[3] OpenVPN allows peers to authenticate each other using a pre-shared secret key, certificates, or username/password. When used in a multiclient-server configuration, it allows the server to release an authentication certificate for every client, using signature and Certificate authority. It uses the OpenSSL encryption library extensively, as well as the SSLv3/TLSv1 protocol, and contains many security and control features.
System requirements:
- A Dedicated server running CentOS 6.x
- Proper knowledge to use Putty and SSH protocol.
How to Install OpenVPN to Build a CentOS VPN server
Prerequisite
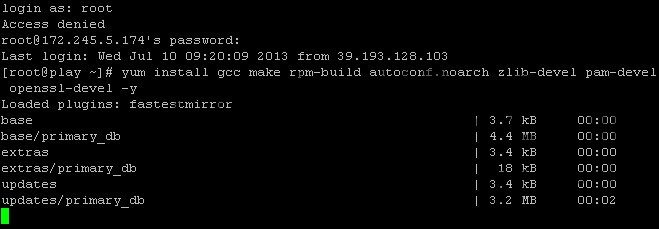
Step 0 – Login to your server via SSH. Best login as root.
Step 1 – Now issue this first command syntax:
yum install gcc make rpm-build autoconf.noarch zlib-devel pam-devel openssl-devel -y
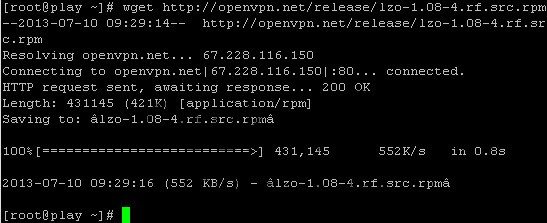
Step 2 – Now download LZO RPM and Configure RPMForge Repo. Use wget command:
wget https://openvpn.net/release/lzo-1.08-4.rf.src.rpm
Step 3 – Now add correct repo for your server:
CentOS 6 32-bit (x86):
wget https://pkgs.repoforge.org/rpmforge-release/rpmforge-release-0.5.2-1.el6.rf.i686.rpm
Or: CentOS 6 64-bit (x86_64):
wget https://pkgs.repoforge.org/rpmforge-release/rpmforge-release-0.5.2-2.el6.rf.x86_64.rpm
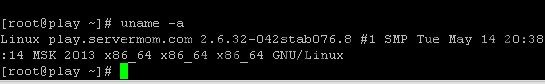
How to know which one is your server? Issue this command:
uname -a
If you see “x86_64 GNU/Linux” at the end of the output line means your server is 64-bit. Otherwise if you see “i686 i386 GNU/Linux” or “x86 GNU/Linux” means your machine is 32-bit.
Step 4 – Then build the rpm package using this command:
rpmbuild --rebuild lzo-1.08-4.rf.src.rpm rpm -Uvh lzo-*.rpm rpm -Uvh rpmforge-release*
hit enter for each line above.
Installing OpenVPN
Step 5 – Issue the special yum command:
yum install openvpn -y
Step 6 – Copy the easy-rsa folder to /etc/openvpn/, use this command:
cp -R /usr/share/doc/openvpn-2.2.2/easy-rsa/ /etc/openvpn/
It seems like in the new version of OpenVPN (2.3.2) easy-rsa is not included, thus, here’s a download link: https://snk.to/f-ch2svs03
Step 7 – Now edit it:
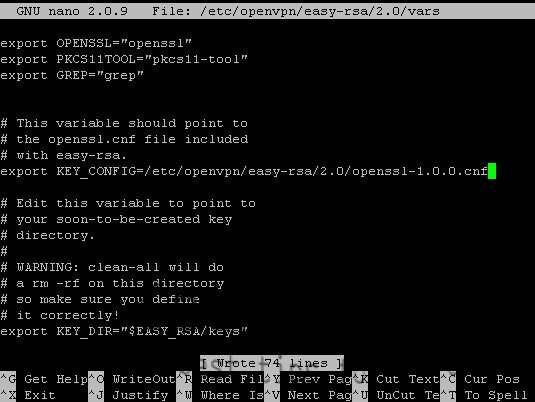
nano /etc/openvpn/easy-rsa/2.0/vars
Edit this line:
export KEY_CONFIG='$EASY_RSA/whichopensslcnf $EASY_RSA'
And replace it with this line:
export KEY_CONFIG=/etc/openvpn/easy-rsa/2.0/openssl-1.0.0.cnf
once done hit Control+O to save then Control+X to exit.
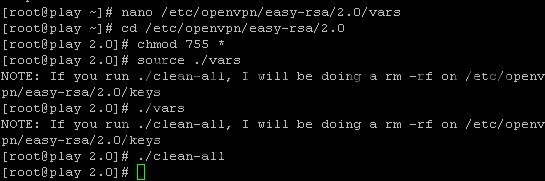
Step 8 – Create the certificate using these commands:
cd /etc/openvpn/easy-rsa/2.0 chmod 755 * source ./vars ./vars ./clean-all
hit enter for each line.
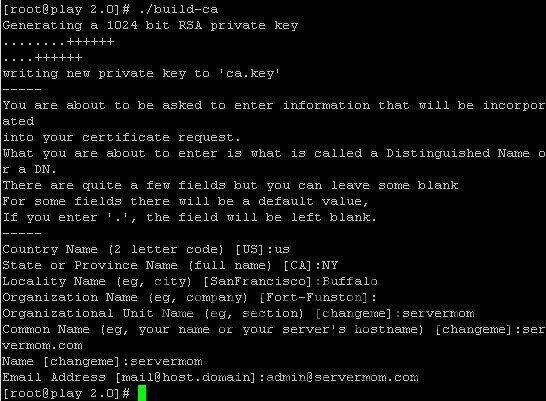
Step 9 – It’s time to build necessary CA file:
./build-ca
Hint Country Name: may be filled or press enter State or Province Name: may be filled or press enter City: may be filled or press enter Org Name: may be filled or press enter Org Unit Name: may be filled or press enter Common Name: your server hostname Email Address: may be filled or press enter
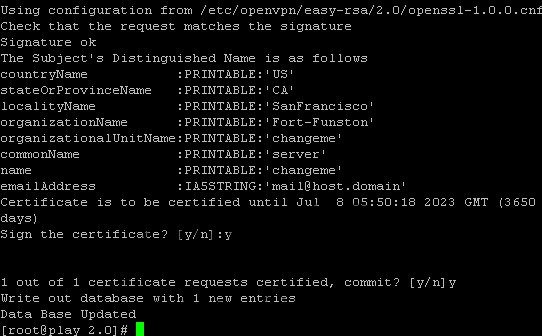
Step 10 – Time to build Key Server:
./build-key-server server
Hint: Almost the same with ./build.ca but check the changes and additional Common Name: server A challenge password: leave Optional company name: fill or enter sign the certificate: y 1 out of 1 certificate requests: y You can simply leave them blank. The only 2 required are sign the certificate (choose “y”) and 1 out of 1 certificate requests (choose “y”)
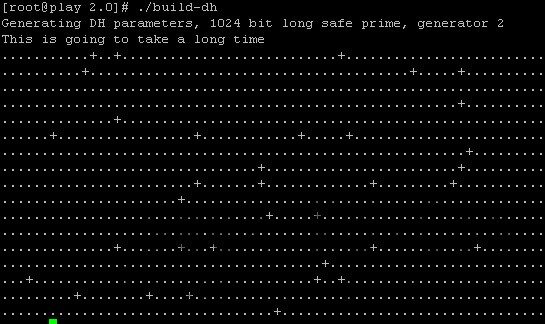
Step 11 – Now issue command below to build Diffie Hellman:
./build-dh
Step 12 – Create OpenVPN config file:
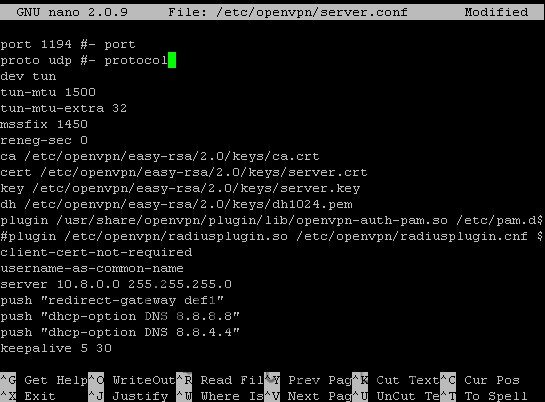
nano /etc/openvpn/server.conf
Step 13 – Now copy and paste these values into the config file:
port 1194 #- port proto udp #- protocol dev tun tun-mtu 1500 tun-mtu-extra 32 mssfix 1450 reneg-sec 0 ca /etc/openvpn/easy-rsa/2.0/keys/ca.crt cert /etc/openvpn/easy-rsa/2.0/keys/server.crt key /etc/openvpn/easy-rsa/2.0/keys/server.key dh /etc/openvpn/easy-rsa/2.0/keys/dh1024.pem plugin /usr/share/openvpn/plugin/lib/openvpn-auth-pam.so /etc/pam.d/login #- Comment this line if you are using FreeRADIUS #plugin /etc/openvpn/radiusplugin.so /etc/openvpn/radiusplugin.cnf #- Uncomment this line if you are using FreeRADIUS client-cert-not-required username-as-common-name server 10.8.0.0 255.255.255.0 push "redirect-gateway def1" push "dhcp-option DNS 8.8.8.8" push "dhcp-option DNS 8.8.4.4" keepalive 5 30 comp-lzo persist-key persist-tun status 1194.log verb 3
Save it once done. (Control+O then Control+X)
- How To: Install and configure OpenVPN on CentOS 6.x
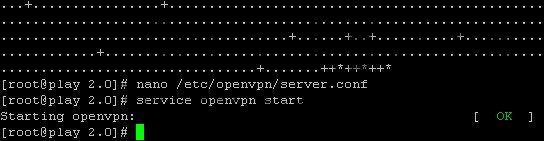
Step 14 – Lets start OpenVPN service on your server for the very first time:
service openvpn start
- How To: Install and configure OpenVPN on CentOS 6.x
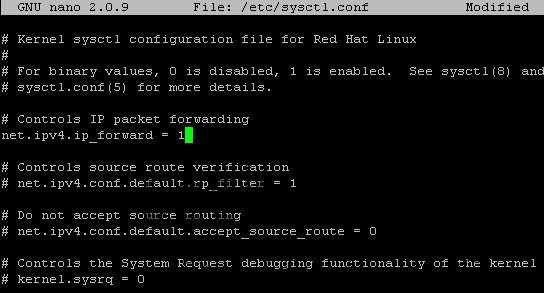
Step 15 – You’ll also need to enable IP forwarding in the file /etc/sysctl.conf. Open it and edit “net.ipv4.ip_forward” line to 1:
nano /etc/sysctl.conf
replace 0 with 1 in this line:
net.ipv4.ip_forward = 1
Hit Control+O to save then Control+X to exit nano.
Step 16 – Issue this command to load the change:
sysctl -p
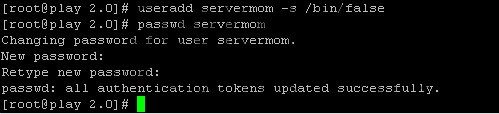
Step 17 – Create new Linux username which can also be used to login to the VPN:
useradd username -s /bin/false
replace username with your own username. Then also create its password:
passwd username
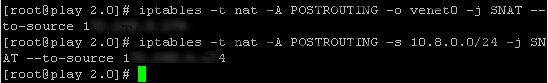
Step 18 – Now route some iptables.
Xen and KVM users use:
iptables -t nat -A POSTROUTING -s 10.8.0.0/24 -o eth0 -j MASQUERADE
iptables -t nat -A POSTROUTING -o venet0 -j SNAT --to-source 123.123.123.123
iptables -t nat -A POSTROUTING -s 10.8.0.0/24 -j SNAT --to-source 123.123.123.123Do not forget to replace 123.123.123.123 with your server IP.
How To: Install and configure OpenVPN on CentOS 6.x
Step 19 – Note: if you have CSF on the same server you need to open your OpenVPN port (Usually 1194) through the firewall and run the below commands for CSF:
iptables -A FORWARD -m state --state RELATED,ESTABLISHED -j ACCEPT iptables -A FORWARD -s 10.8.0.0/24 -j ACCEPT iptables -A FORWARD -j REJECT iptables -t nat -A POSTROUTING -s 10.8.0.0/24 -o eth0 -j MASQUERADE iptables -t nat -A POSTROUTING -j SNAT --to-source 123.123.123.123
Step 20 – Now save that iptables rules:
service iptables save
Step 21 – Windows VPN client installation, lets create a server.ovpn config file. To make it easy, you can simply create it on your local computer using Notepad (or any other simple text editor tool). Enter following in that file:
client dev tun proto udp remote 123.123.123.123 1194 # - Your server IP and OpenVPN Port resolv-retry infinite nobind tun-mtu 1500 tun-mtu-extra 32 mssfix 1450 persist-key persist-tun ca ca.crt auth-user-pass comp-lzo reneg-sec 0 verb 3
Then save it with .ovpn extension. Save that file in the config directory of where you installed OpenVPN client in your computer. See
Step 22 – That’s it. Now you can copy ca.crt file from /etc/openvpn/easy-rsa/2.0/keys/ directory and place it in your server’s document root (public_html).
cp /etc/openvpn/easy-rsa/2.0/keys/ca.crt /path/to/public/directory
example:
cp /etc/openvpn/easy-rsa/2.0/keys/ca.crt /var/www/www.geek-kb.com/public_html
Now you can download the ca.crt file from your browser by going to domain.com/ca.crt then save it to the same folder as .ovpn file you created earlier. That’s it. Now you can login to your VPN using username and password you’ve created.
Step 23 – Ubuntu VPN client installation:
Install openvpn:
yum install openvpn -y
Next, copy ca.crt, username.key, and username.crt from the OpenVPN server to your Ubuntu machine.
Step 24 – Configure the client
Create a new config file called server.conf for example and paste these values into it (don’t forget to replace 123.123.123.123 with your OpenVPN server IP and also point the red marked lines to the relative path of your ca.crt, username.key, and username.crt ):
client itaig-lt dev tun proto udp remote 123.123.123.123 1194 resolv-retry infinite nobind persist-key persist-tun comp-lzo verb 3 ca "/etc/openvpn/homecerts/ca.crt" cert "/etc/openvpn/homecerts/itaig-lt.crt" key "/etc/openvpn/homecerts/itaig-lt.key"
Next, move the server.conf file to /etc/openvpn and restart the service:
service openvpn restart
There’s one more thing remaining to do on machines in the remote VPN network:
On each machine you intend to connect to remotely, you have to add the relevant route (if you have a router in the remote network you can simply add the route there):
On a Linux machine:
# route add -net net.id/network.size gw ip.of.gateway metric 1
Example:
# route add -net 192.168.1.0/24 gw 192.168.0.100 metric 1
After adding the route, test to see if it works by using ping on an IP on the remote network and if it works then you should set it as a permanent route. To do that, create a file in /etc/sysconfig/network-scripts/ folder and name it route-dev_name (the device which resides on the network you routed). Example:
nano /etc/sysconfig/network-scripts/route-eth0
And then type into the file the route line, it should look like that:
192.168.1.0/24 via 192.168.0.100 dev eth0
Hit ‘Ctrl + X’ to save the file.
On a Windows machine:
c:\route add net.id mask network.mask gateway.ip
Example:
c:\route add 192.168.1.0 mask 255.255.255.0 192.168.0.100
As mentioned above, after adding the route, test to see if it works by using ping on an IP on the remote network and if it works then you should set it as a permanent route. To do that, run the same command again and add -p at the end of the line, like so:
c:\route add 192.168.1.0 mask 255.255.255.0 192.168.0.100 -p
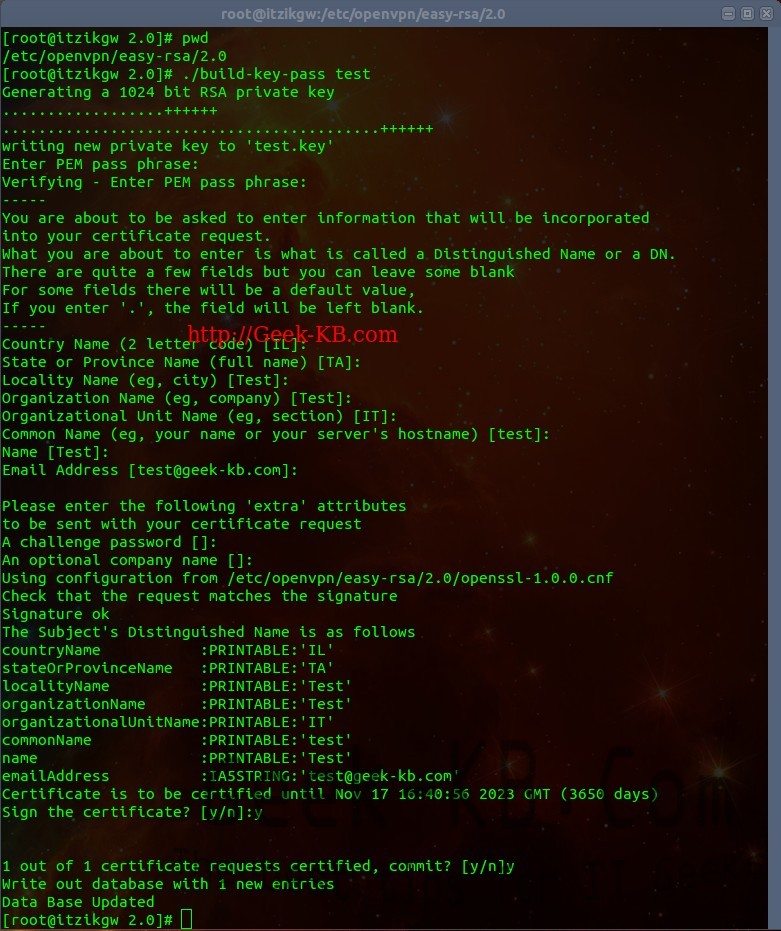
Optional section (password protect your certificate):
If you would like your users to use a password protected certificate when connecting to your VPN server, follow the next steps: 1. Go to:
/etc/openvpn/easy-rsa/2.0
2. Edit the vars file as mentioned above. 3. Run:
# source ./vars # ./build-key-pass user_name
The password the user will have to input is the “PEM pass phrase”
4. Now copy the user.crt, user.key and ca.crt to the relevant folder on the client and edit your .ovpn file on Windows or server.conf in Linux to add the new files. 5. Connect. I hope this guide helped you, feel free to leave comments or ask questions.


No Comments Yet