This article is part 3 in a series of 3 articles regarding 18 Linux system monitoring tools you should know.
In this article we’re going to cover some built-in system monitoring tools as well as some free add-on tools
which will make your life easier when troubleshooting issues regarding Networking in your server.
You are browsing archives for
Author: Itai Ganot
Linux System Monitoring tools you should...
This article is part 2 in a series of 3 articles regarding 18 Linux system monitoring tools you should know.
In this article we’re going to cover some built-in system monitoring tools as well as some free add-on tools which will make your life easier when troubleshooting issues regarding System.
Set a static route in CentOS/RHEL 6.x
In this article, How To set a static route in CentOS/RHEL 6.x I will explain when it is necessary to use a static route and how to set it up. Static routing is a type of method of network routing. Static routing in not actually a routing protocol a manual configuration on the network route. […]
Linux Memory and Process monitoring tool...
This article is part 1 in a series of 3 articles regarding 18 Linux system monitoring tools you should know.
In this article we’re going to cover some built-in system monitoring tools as well as some open source add-on tools
which will make your life easier when troubleshooting issues regarding Memory and Processes in your server.
Most Linux distributions are equipped with many monitoring tools.
These monitoring tools provide metrics which can be used to get information about system activities, such as Disk (storage) usage, CPU and memory, or Network bottlenecks.
You can use the monitoring tools to find the possible causes of a performance issue.
The commands discussed in this article are some of the most basic monitoring commands when it comes to
system analysis and debugging server issues such as:
Finding out bottlenecks.
Disk (storage) bottlenecks.
CPU and memory bottlenecks.
Network bottlenecks.
Setup Open Source Pure-FTPd with MySQL o...
Pure-FTPd is a free and secure FTP server. It provides efficiency and ease of use, simple answers to common needs, plus unique useful features for personal users as well as hosting providers. This how to guide will help you to setup Pure-FTPd with MySQL as user database. Also providing detailed instruction to create a user […]
Hack WEP protected wireless in 5 easy st...
1. The articles contained on the website are for educational purposes only encouraging users and Admins to better understand the environmental security measurement and enable safer digital environment.
Geek-KB.com does not encourage, condone, or orchestrate attempts of hacking into other servers or any other illegal activities. All actions taken by users are strictly independent of Geek-KB.com. We are not responsible for any misuse of the techniques listed on this website.
2. Geek-KB.com has the sole discretion to remove/edit users, articles, external resources, or any other user-submitted content to protect itself from legal harm. This legal disclaimer may be modified at any time without notice.
3. Any damage caused by using any of the techniques taken from https://www.geek-kb.com is at your own risk and responsibility;
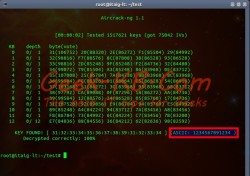
For this article I’m using Aircrack-ng tool set which can be downloaded for free from their site and can be installed on all Linux distributions as well as on Windows, but for this article I will show examples using my Ubuntu laptop installed with Aircrack-ng which I’ve downloaded from the default APT repositories.
Since it is well known that WEP is not a secured method to secure your network it is less seen as time passes, but some businesses still do and here we will show you how it can be hacked and and it’s password can be gained.
System Requirements:
A Linux machine installed with Aircrack-ng (can be downloaded from here).
A Wireless network adapter which has the ‘Packet Injection’ feature, a list of supported cards can be found here.
How To: Upgrade CentOS Linux v6.x to v6....
[ hana-code-insert ] ‘468×15’ is not found usage: CentOS Linux v6.5 has been released recently and it is available via repositories for immediate update. The new CentOS versions includes several hundred bug fixes for, and enhancements to the Linux kernel. If you would like to know how to Upgrade CentOS Linux v6.x to v6.5, then keep […]