Recently, a serious vulnerability has been discovered in the very popular OpenSSL cryptographic software library known as the heartbleed bug. This weakness allows a malicious user to steal information protected, under normal conditions, by the SSL/TLS encryption used to secure the Internet. Transport Layer Security (TLS) and its predecessor, Secure Sockets Layer (SSL), are cryptographic […]
You are browsing archives for
Category: Hacking tools
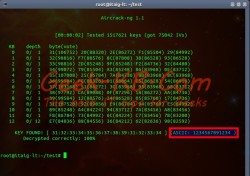
Aircrack-ng tool installed on all Linux distributions as well as on Windows, install Reaver on Ubuntu 12.04 or later, gain full access privileges to windows machine with generated exploited executable file and more
Hack WEP protected wireless in 5 easy st...
1. The articles contained on the website are for educational purposes only encouraging users and Admins to better understand the environmental security measurement and enable safer digital environment.
Geek-KB.com does not encourage, condone, or orchestrate attempts of hacking into other servers or any other illegal activities. All actions taken by users are strictly independent of Geek-KB.com. We are not responsible for any misuse of the techniques listed on this website.
2. Geek-KB.com has the sole discretion to remove/edit users, articles, external resources, or any other user-submitted content to protect itself from legal harm. This legal disclaimer may be modified at any time without notice.
3. Any damage caused by using any of the techniques taken from https://www.geek-kb.com is at your own risk and responsibility;
For this article I’m using Aircrack-ng tool set which can be downloaded for free from their site and can be installed on all Linux distributions as well as on Windows, but for this article I will show examples using my Ubuntu laptop installed with Aircrack-ng which I’ve downloaded from the default APT repositories.
Since it is well known that WEP is not a secured method to secure your network it is less seen as time passes, but some businesses still do and here we will show you how it can be hacked and and it’s password can be gained.
System Requirements:
A Linux machine installed with Aircrack-ng (can be downloaded from here).
A Wireless network adapter which has the ‘Packet Injection’ feature, a list of supported cards can be found here.
How To: Generate a payloaded executable ...
1. The articles contained on the website are for educational purposes only encouraging users and Admins to better understand the environmental security measurement and enable safer digital environment.
Geek-KB.com does not encourage, condone, or orchestrate attempts of hacking into other servers or any other illegal activities. All actions taken by users are strictly independent of Geek-KB.com. We are not responsible for any misuse of the techniques listed on this website.
2. Geek-KB.com has the sole discretion to remove/edit users, articles, external resources, or any other user-submitted content to protect itself from legal harm. This legal disclaimer may be modified at any time without notice.
3. Any damage caused by using any of the techniques taken from https://www.geek-kb.com is at your own risk and responsibility;
Metasploit Framework installation
1. The articles contained on the website are for educational purposes only encouraging users and Admins to better understand the environmental security measurement and enable safer digital environment.
Geek-KB.com does not encourage, condone, or orchestrate attempts of hacking into other servers or any other illegal activities. All actions taken by users are strictly independent of Geek-KB.com. We are not responsible for any misuse of the techniques listed on this website.
2. Geek-KB.com has the sole discretion to remove/edit users, articles, external resources, or any other user-submitted content to protect itself from legal harm. This legal disclaimer may be modified at any time without notice.
3. Any damage caused by using any of the techniques taken from https://www.geek-kb.com is at your own risk and responsibility;
How To: Generate Rainbow Tables Using Wi...
1. The articles contained on the website are for educational purposes only encouraging users and Admins to better understand the environmental security measurement and enable safer digital environment.
Geek-KB.com does not encourage, condone, or orchestrate attempts of hacking into other servers or any other illegal activities. All actions taken by users are strictly independent of Geek-KB.com. We are not responsible for any misuse of the techniques listed on this website.
2. Geek-KB.com has the sole discretion to remove/edit users, articles, external resources, or any other user-submitted content to protect itself from legal harm. This legal disclaimer may be modified at any time without notice.
3. Any damage caused by using any of the techniques taken from https://www.geek-kb.com is at your own risk and responsibility;
NjRAT setup:Hack Facebook, Twitter, Payp...
Tutorial: Setup NjRAT and Hack Facebook, Twitter, Paypal Password RAT, as we all know, is Remote Administration Tool. A tool which is used to hack computers remotely. It is mostly used for malicious purposes, such as controlling PC’s, stealing victims data, deleting or editing some files. You can only infect someone by sending him file […]